I would like to clarify – at no point have I tried to actually phish details, tamper with votes, see how people vote, access Edugates database, bring the site down, or prevent the preferendum from occurring.
My intentions are to a) see how secure the voting process is, and b) see if any security issues could be used for fraudlent means.
Most people usually welcome security audits of voting practices, except those in power.
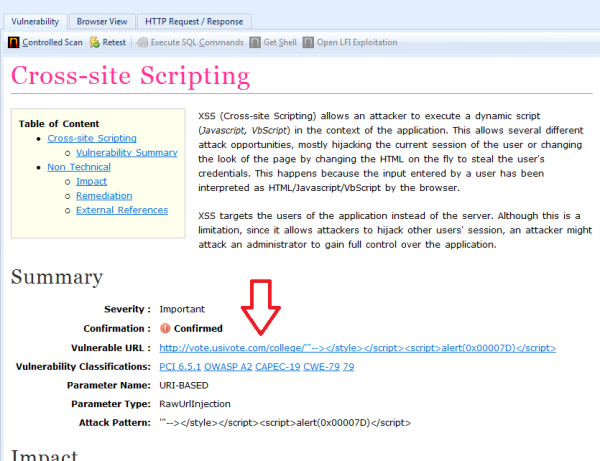
Before any online voting system was launched, a basic security audit should have been carried out. That doesn’t appear to have happened, or if it did, it was inadequate – so I carried out my own.
Gary Redmond has dismissed the issue the xss issue I posted about on Saturday, and claimed that this is similar to phishing for online bank details.
Presumably the assumption is that the same thing can occur in online banking, and therefore, USIs voting system is as secure as online banking, or using an ATM machine.
If that is the assumption, it’s demonstrably wrong.
2 Factor Authentication (2FA) for n00bs
The xss & phishing process, documented on Saturday, and in the video above, isn’t possible in online banking, because online banking requires what the security community call 2 Factor Authentication (2FA).
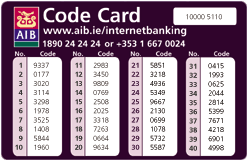
For example, with AIB online banking, you get a code card , and need to enter 2 additional codes every time you use it – in addition to your login details (there’s also a personal card reader).
The 2 Factors for authentication are therefore:
- login details (something you know), and
- the code card (something you have).
If someone tried to phish your AIB Registration Number and Personal Access Code, they still couldn’t access your online banking because they wouldn’t know the 2 random codes they would require from the code card – only you have the code card for numbers.
(Also, banks hire developers who can correctly code forms to prevent xss issues in the first place).
What makes online banking more secure from issues like xss & phishing, is 2 Factor Authentication.
What makes makes USIs system less secure is that it only uses 1 Factor Authentication – login details.
SU Elections, Referenda and 2FA:
Even the long established method of paper ballots uses 2 Factor Authentication – id & and a polling clerk to check that you’re the person the id belongs to.
Factor 1: If you don’t have id, you can’t vote.
Factor 2: If the person handing over the id doesn’t match the photo of person on the card, they can’t vote. This helps prevent impersonation – the major flaw in USIs online voting system.
If you aim to be secure, use at least 2FA. Examples:
- Credit card in a shop: credit card (something you have) and PIN number (something you know)
- ATM machine: ATM card (something you have) and PIN number (something you know)
- Online banking: AIB code card (something you have), login details (something you know).
- Manual cash withdrawal from a bank: id (something you have), being present to hand over the id so a bank employee can check that you are the person in the id (something you are), and bank account details (something you know).
- SU elections, referenda, local elections, general elections etc: id (something you have), a polling clerk to check that you’re the person the id belongs to (something you are).
- USI online vote: valid login details (something you know, and I can know through xss), and……….nothing else? Spot the odd one out?
Edugate can check that you have functioning login details, but it can’t check that those valid login details are actually yours.
If I phish, steal, or simply know your login details – I can use your online vote (impersonation).
With a a regular paper ballot, if I find, borrow, or steal your student card, I can’t vote – because I’m obviously not the person on the id.
This is a basic safeguard against impersonation that’s built into most credible voting systems – but not USIs.
It’s even possible to cast fraudulent votes in the preferendum without knowing someones login details, due to Edugates use of Single Sign-On (SSO) – but I’ll come back to that later.
Bizarrely, at a time when most companies & organisations (including Google, Facebook, and Yahoo) are moving away from 1 factor authentication due to the obvious flaws , USI have decided to move towards it while claiming it to be more secure.
The issue is not whether Edugates database can be compromised or not – that’s a straw man argument.
The issue is the flawed voting system; there is no protection from impersonation – i.e, someone other than you can use your login details to cast fraudulent votes.
There are protections against impersonation in a normal vote with paper ballots, as explained earlier.
Fraping and SSO
(Study Finds Major Weaknesses in Single Sign-on Systems (March 2012) –
http://www.pcworld.com/businesscenter/article/252656/study_finds_major_weaknesses_in_single_signon_systems.htm )
Even if you don’t believe me about the security issues on USIs website – how xss was possible, and how details could have been stolen to impersonate someone – there is one undeniably simple method of casting a fraudulent vote, which USI are aware of.
Edugate uses a system called Single Sign-On (SSO). This means that if you’re logged into one Edugate service , you don’t need to login to access another Edugate service. You can see this in the video I made of the voting process – I don’t need to enter my login details in order to vote because I was already logged in to Edugate.
If you’re logged in to a pc in college, and leave it to go to the toilet, anyone can walk up to that pc & use your vote in the preferendum.
If you’re logged in to the online library on your laptop in your flat, and leave it unattended, anyone can walk up to that laptop & use your vote in the preferendum.
If you’ve been fraped, or have fraped someone, you’ll know that this is easy.
Edugate is as secure from fraudulent votes, as Facebook is from fraping.
Basically, the Edu’gate’ is wide open (I know, sorry).
USI will undoubtedly claim that the repsonibility is with the student not to leave their computer unattended, to ensure that they log out, and to protect their login details – that’s true, but USI also have a responsibility to put in place a safeguard against impersonation, and they haven’t.
In normal elections & referenda, that protection comes from both having a valid student card, and having someone to check that you are the person pictured in the student card (2FA) .
A system of voting which fails to put up a safeguard against impersonation (again, 2 Factor authentication), simply cannot be regarded as credible.
E-voting machines were bad, USIs Fees Preferendum is much worse
 Even with the widely derided e-voting machines, which the government scrapped, 2 Factor Authentication was still required.
Even with the widely derided e-voting machines, which the government scrapped, 2 Factor Authentication was still required.
For blindingly obvious reasons, a polling clerk had to check that you had valid id, and that that the id was yours.
It wasn’t possible to simply walk up to the machine, enter login details, and vote .
Yet this is essentially what USI are allowing, and with Edugates SSO, you don’t even need a password in some instances.
A system which was abandoned, and ridiculed, has more integrity than USIs Preferendum.
o
To use this flawed system – on a flawed website with security issues – to make one of the most important decisions in USIs history, would be a mistake.
I strongly urge everyone to 9D this at Special Conference.
**************
More info will be posted later.
https://twitter.com/#!/ThirdLevelFees
PS – common sense suggests that if something password protected, it’s protected for a reason.